5 Simple Ways To Spot a Phishing Email

5 Simple Ways To Spot a Phishing Email
A phishing email is one that has the looks of coming from a reliable source but is actually sent by a malicious party. An attachment or link in a phishing email is intended to deceive the receiver into downloading malware onto their machine. Additionally, important information including credit card details and login details can be stolen through phishing emails.
How can you identify a scam email?
You can detect a phishing email by keeping an eye out for the following signs:
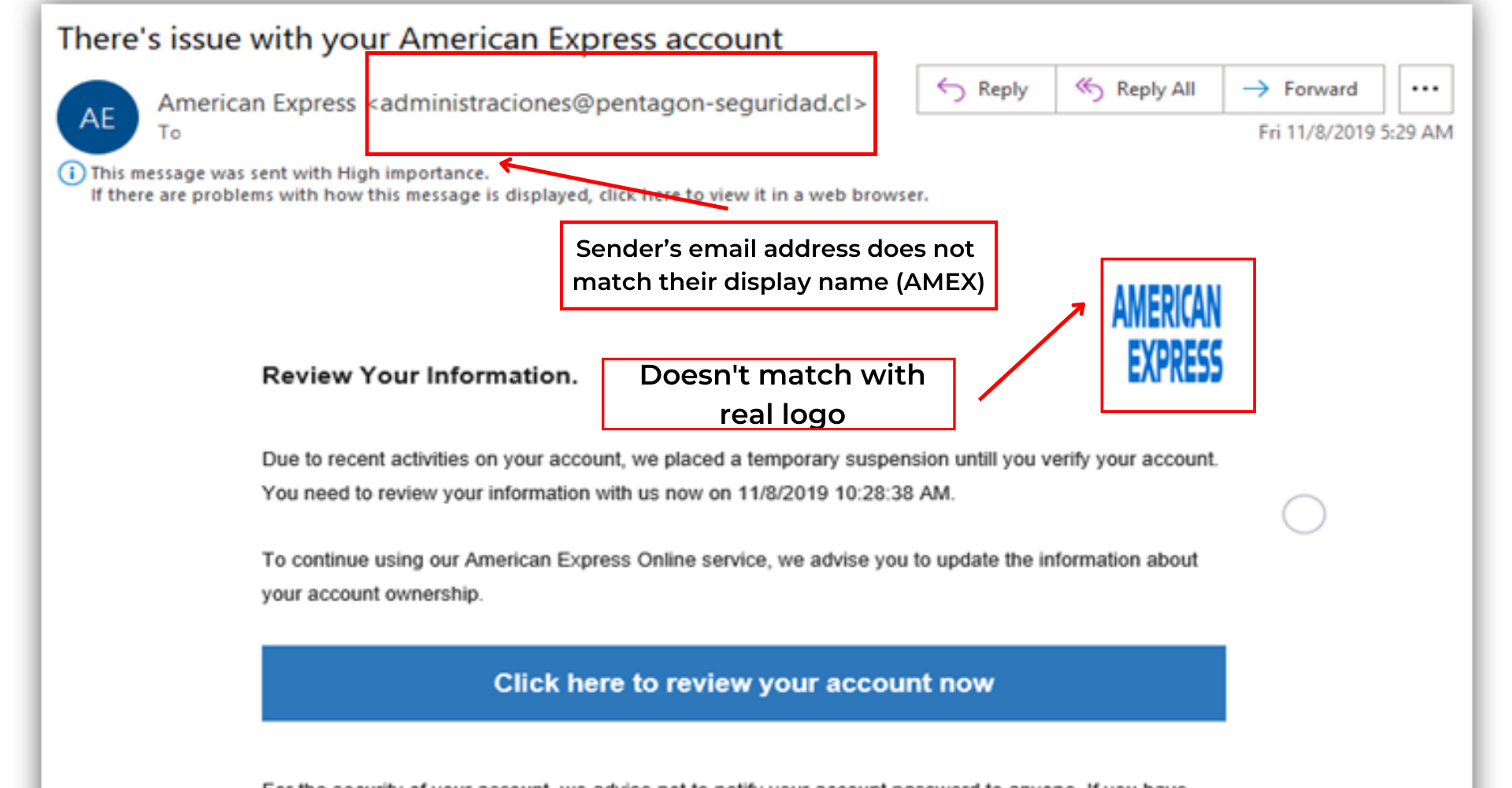
- The email address used by the sender does not belong to the name of the business or organization that they pretend to express.
- The email contains grammatical mistakes or unusual word choices.
- The email makes you feel compelled to act right away by expressing urgency or threatening penalties.
- You weren't hoping the link or attachment was included in the email.
- Simply speaking, the email appears suspicious because it was sent by an unknown source or has an uncomfortable subject line
1) The email address used by the spammer does not correlate to the name of the business or enterprise they tend to show.
Most frequently, phishing emails are sent using bogus email addresses that seem to be from a reliable source. The email address will typically differ somewhat from the authentic address even though the sender's identity may be accurate or the logo is slightly changed.
2) The email has grammatical mistakes or unusual word choices.
Phishing emails frequently have poor writing, including grammatical mistakes or strange wording, or numbering. This is due to the fact that non-native English speakers are typically the ones that generate them quickly. For instance, a phishing email can read: "Please fill this form", "To reactivate it, just click it." or some random numbers are added in a line to complete the mail.

3) The email makes you feel compelled to act right away or threatens you with negative outcomes if you don't.
By promising severe results if you fail to not take rapid action, phishing emails frequently induce a sense of pressure. For instance, a phishing email wants to sign in to your account via some link within a second and threatens to terminate your account whenever you don't clarify your login details in less than 7-14 days.

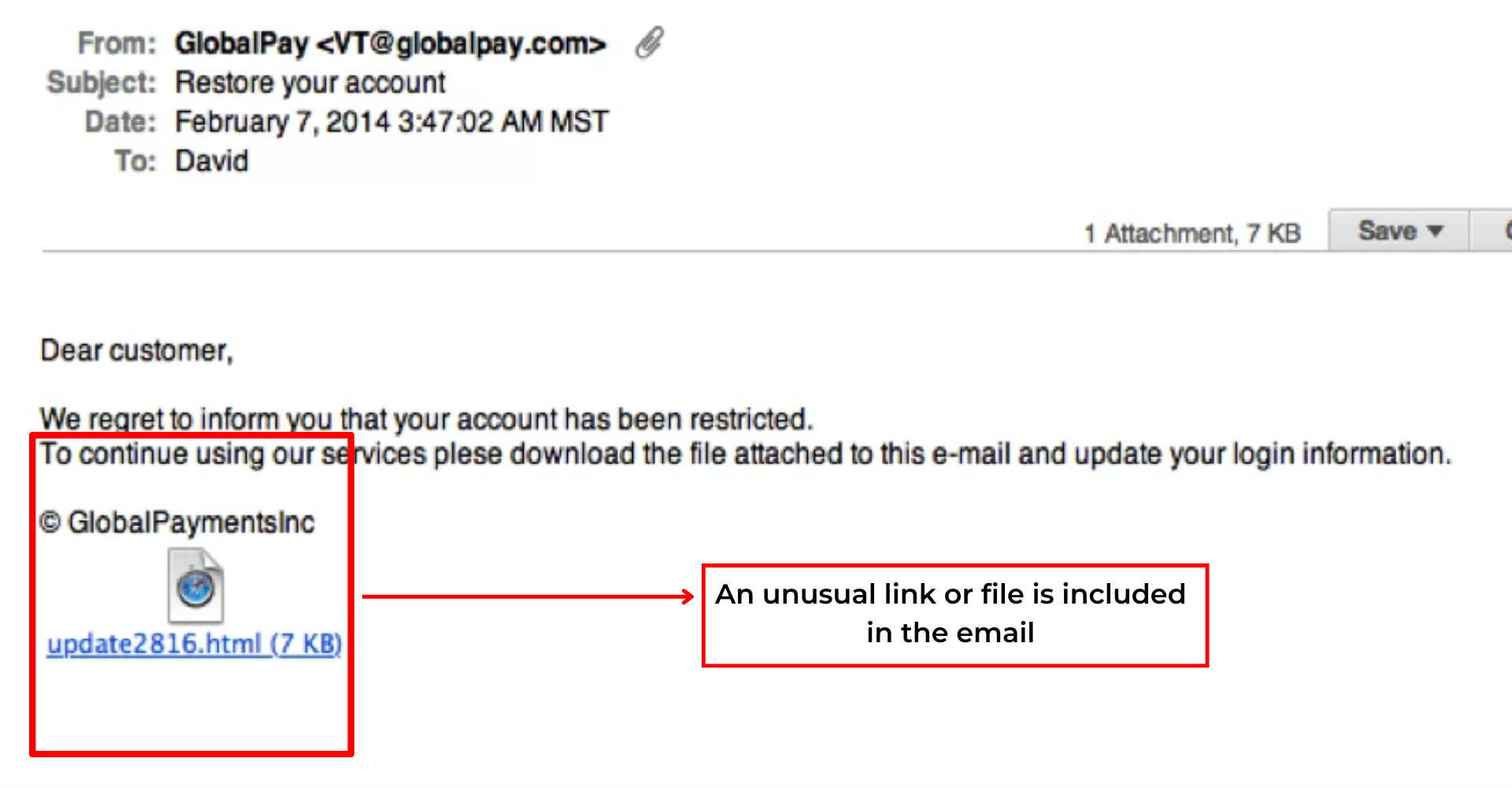
4) An unusual link or file is included in the email.
Phishing emails frequently contain unusual links or attachments. Such links and attachments can infect your computer with malware or lead you to a fraudulent website. Whenever you get an email with a link or file from an anonymous source, don't really click.
5) The email seems strange in context, for instance, the fact that it came from an untrusted source or had an irregular subject line.
An email is probably a phishing email if something appears questionable. Because authentic institutions don’t randomly send you emails with attachments, but instead direct you to download documents or files on their own website. Emails with strange subject lines or unidentified senders may fall under this category. For instance, a phishing email is one containing the subject line "Immediate! Your credit card or bank account has been hacked!" 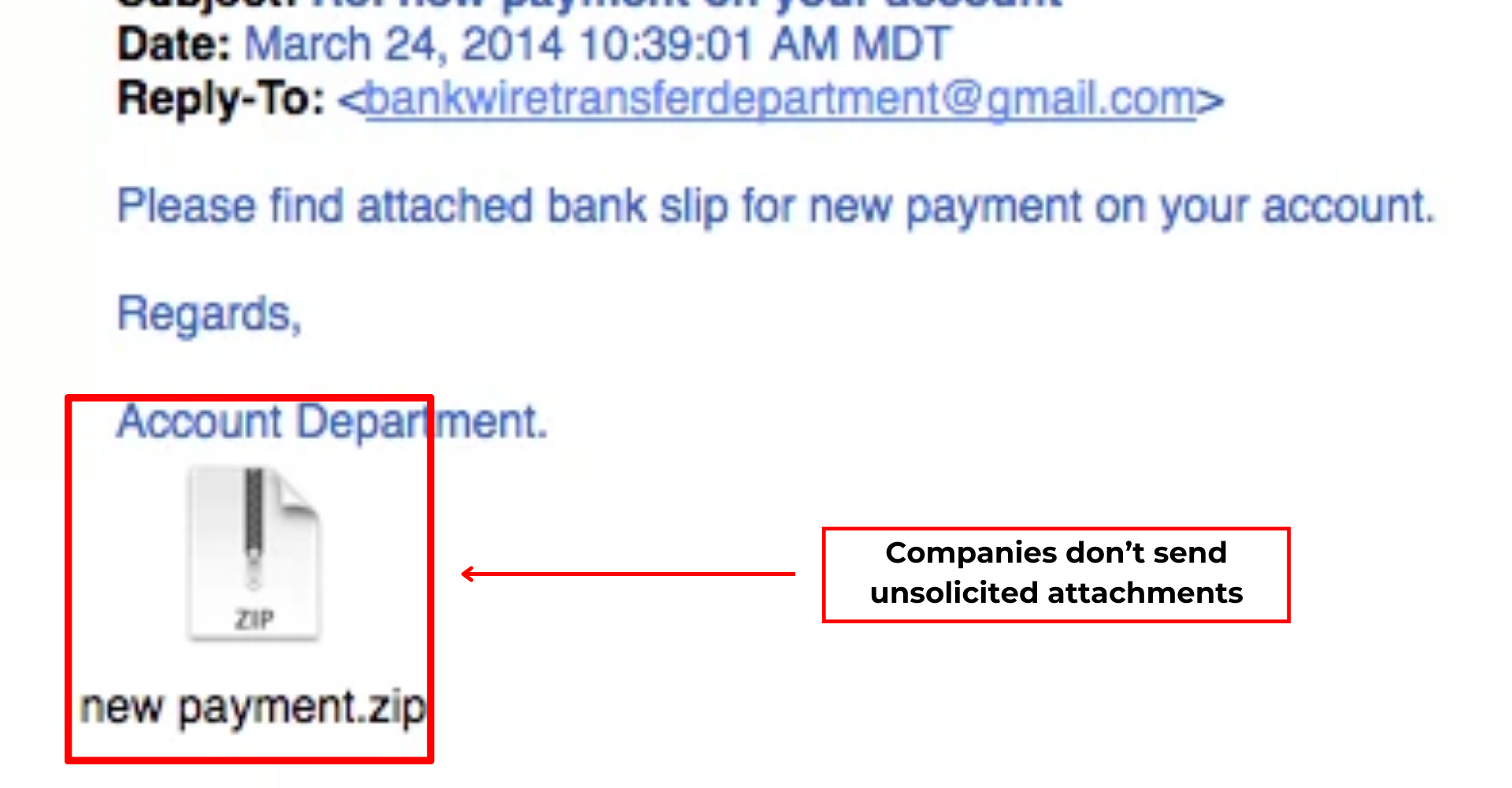
How should you respond to a phishing email?
Avoid clicking any links or downloading any attachments from scam emails. You can get in touch with the business or group immediately to confirm an email's validity if you're not sure if it's real. In addition, you should remove the phishing email from your mailbox and inform your email service provider.
Which of the following phishing email formats are frequent?
Phishing emails typically come in the following forms:
- Fabricated emails appear as coming from a reliable business or authority.
- Emails threaten negative outcomes when you do not respond right away.
- Emails containing files or links that download malware or take you to a harmful website.
- Emails with strange subject lines or unidentified senders.
- Emails that generally seem suspect
Concluding Views:
Cybercriminals frequently use phishing emails to obtain your personal details. There are strategies to recognize fraudulent emails even if they frequently symbolize actual emails quite closely. Avoid clicking any links or downloading any attachments from emails that appear questionable. Rather, file a complaint with the organization to which the email appears to belong.